-
- Introduction
- Setup
- What's new
- Start Window
- Multi-Window System
- Camera
- Objects
- Tools
- Additional objects
- Custom attributes
- Project tree
- Search tab
- Attributes tab
- Files tab
- 2D to 3D projection
- Animation
- AppControls
- Comment
- Drawing
- Markup
- Package
- P&ID Sketch
- Photo
- Point of Interest
- Report
- Screenshot
- Sketch
- Spraying
- View
- Settings
- Advanced options
- IntelliPID Module
- Linking and API
- Appendix - Custom settings files
- Appendix - Command line parameters
- Appendix - Performance optimisation
- Appendix - How to use 3D PDF files
Using federated accounts
You can set up the UPV WebServices account management to be linked with an external authentication provider like f.e. ADFS using one of the different authentication protocols supported by Keycloak. This will delegate the authentication to the referenced identity provider.
This document shows the configuration process on based on the example of Microsoft Azure.
Basic configuration
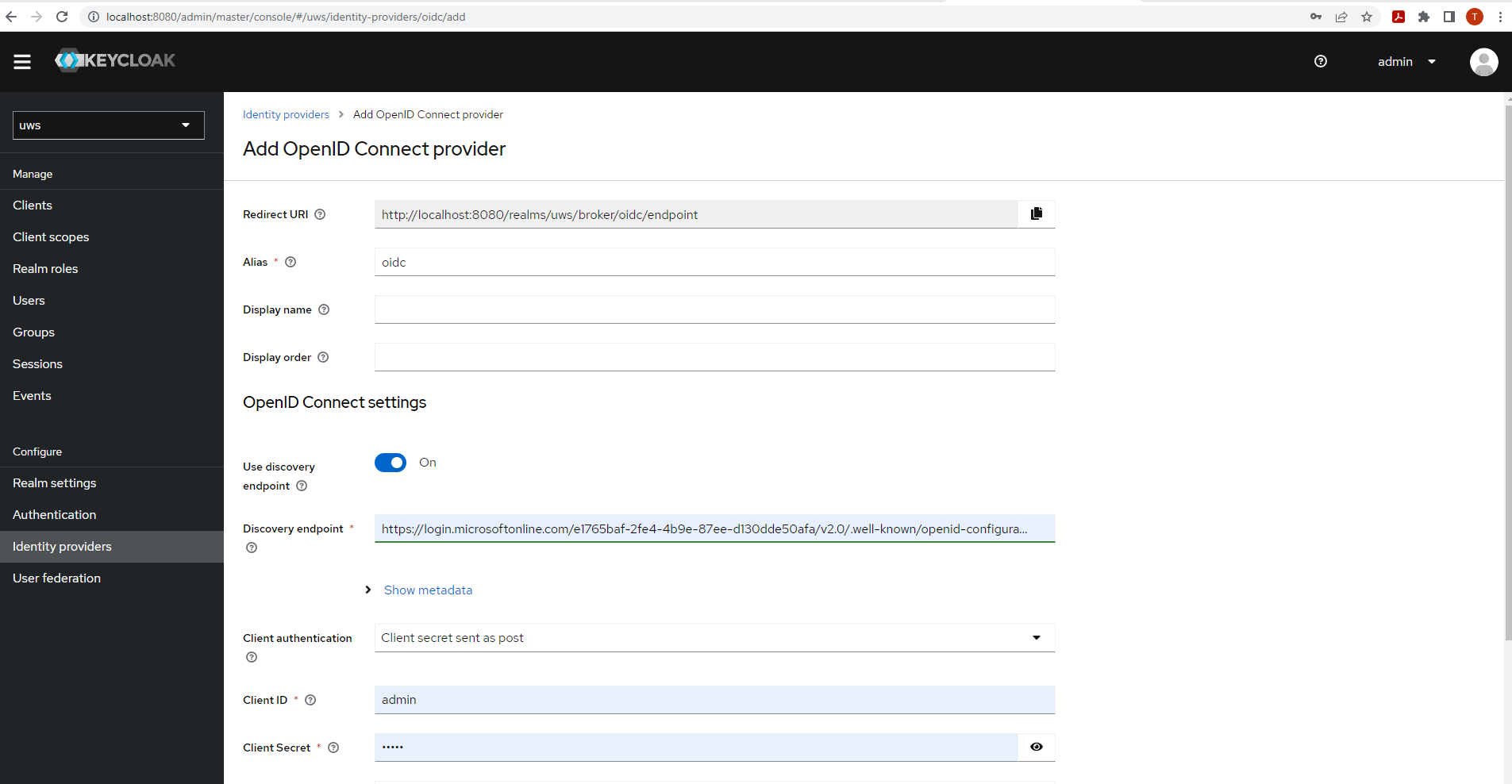
1) Create a new Identity provider entry in the Keycloak administration UI
- Select the application realm (default: uws)
- Go to Configure/Identity providers
- Add new User-defined provider: OpenID Connect v1.0
| Field | Description |
|---|---|
| Alias | Identifies the provider - Can be set freely |
| Discovery endpoint |
Path to the .well-known/openid-configuration - f.e. for Azure ADFS:
https://login.microsoftonline.com/<tenant id>/v2.0/.well-known/openid-configuration
|
| Client ID | Obtained in Azure app registration |
| Client Secret | Can be generated in Azure app registration at Manage/Certificates & secrets |
| Advanced/Backchannel logout (optional) | Recommended to be set to true This ensures when logging out of UWS, it will not log out of the Identity provider as well |
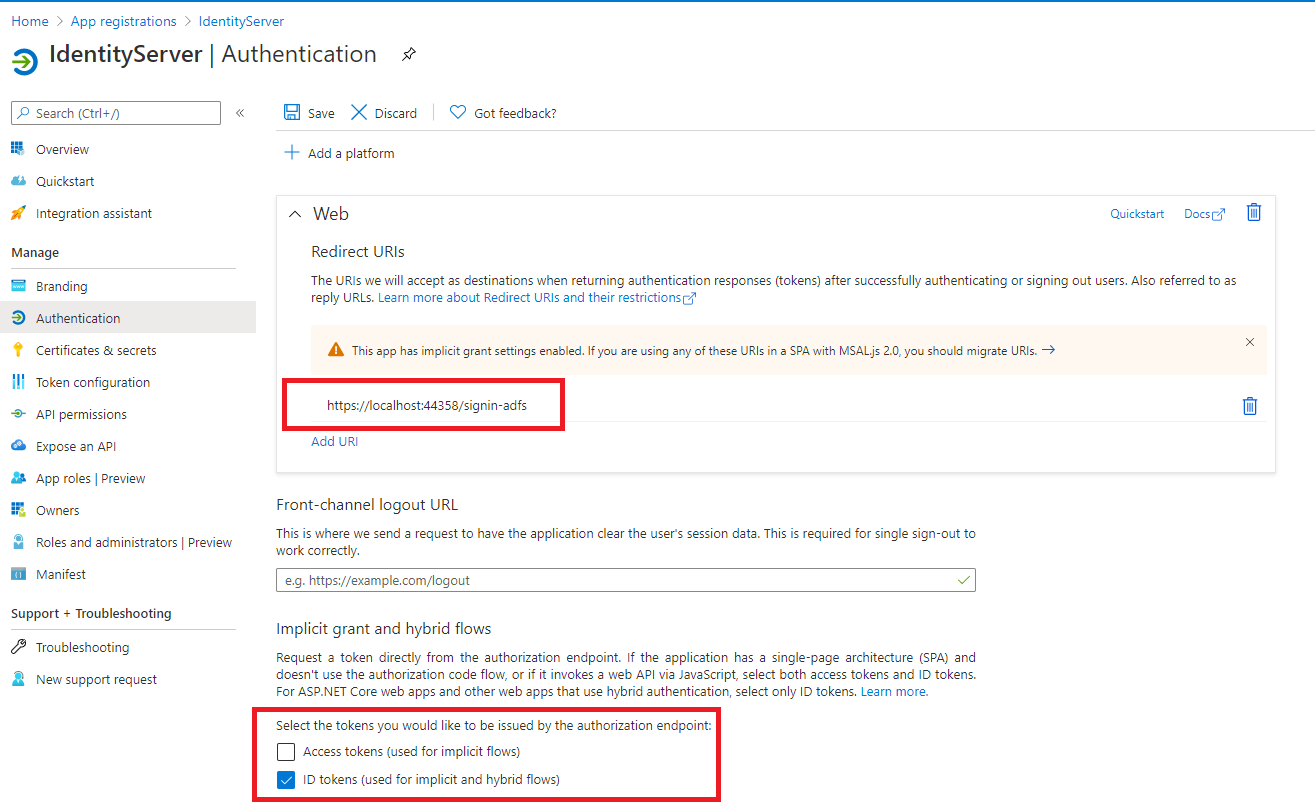
2) Set up a new App registration in Microsoft Azure
Redirect URI: Can be copied from the Keycloak registrations first field
entry - for example
http://localhost:8080/realms/uws/broker/oidc/endpoint
Enable ID tokens
3) Try login in to the UWS There should now be a new login option in the Keycloak login mask
Additional configuration options
Include email metadata
Allow UPV WebServices to extract email address from external provider - The email will be synchronized on each login
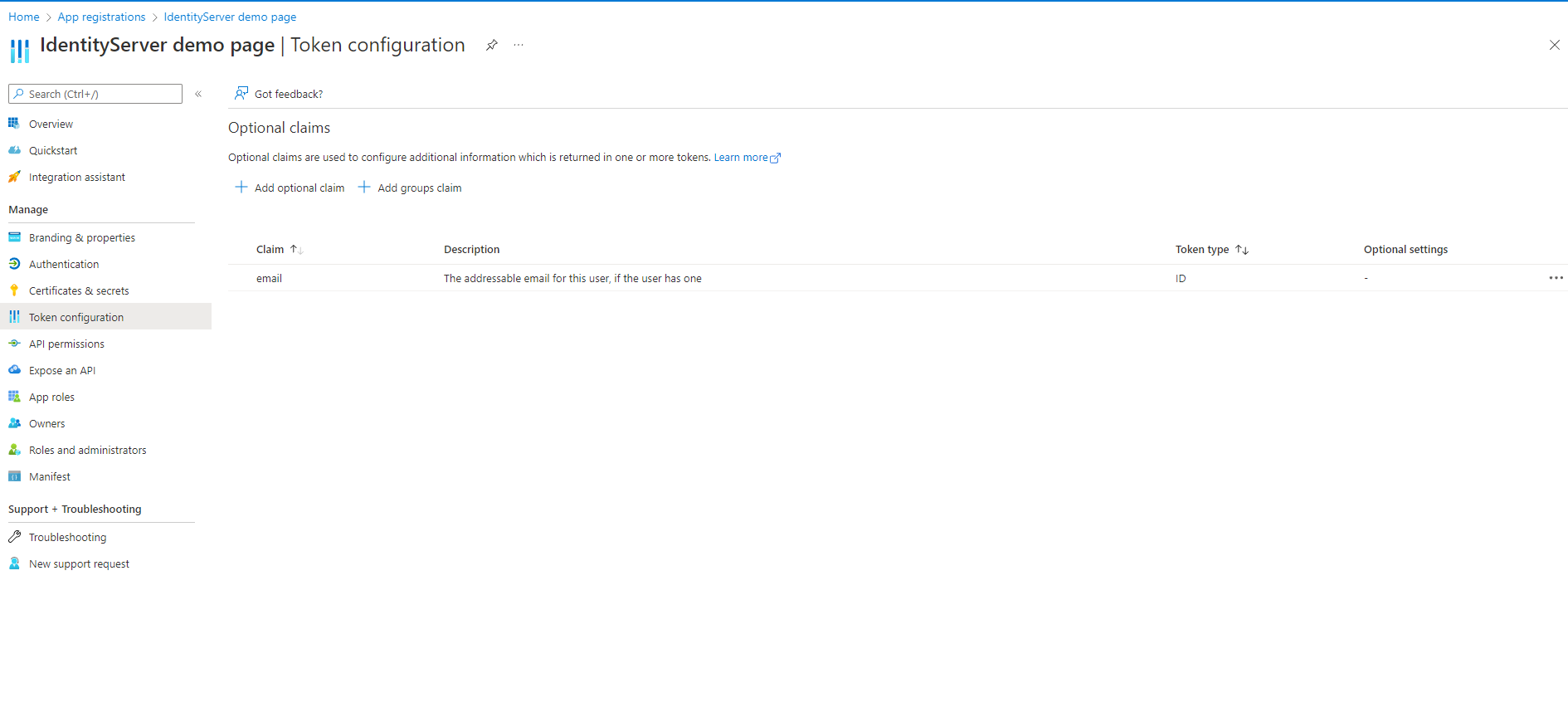
Allow requesting the email claim in the azure portal:
On the Token Configuration page -> add an aditional optional claim -> Token type: ID -> Search the list for email claim
Add the claim in the Identity provider settings in Keycloak:
At Advanced/Scopes add email
Use group synchronization
Allow UPV WebServices to extract user groups from external provider. The user groups will be synchronized when restarting the UWS or calling ForceRefresh in the Admin UI.
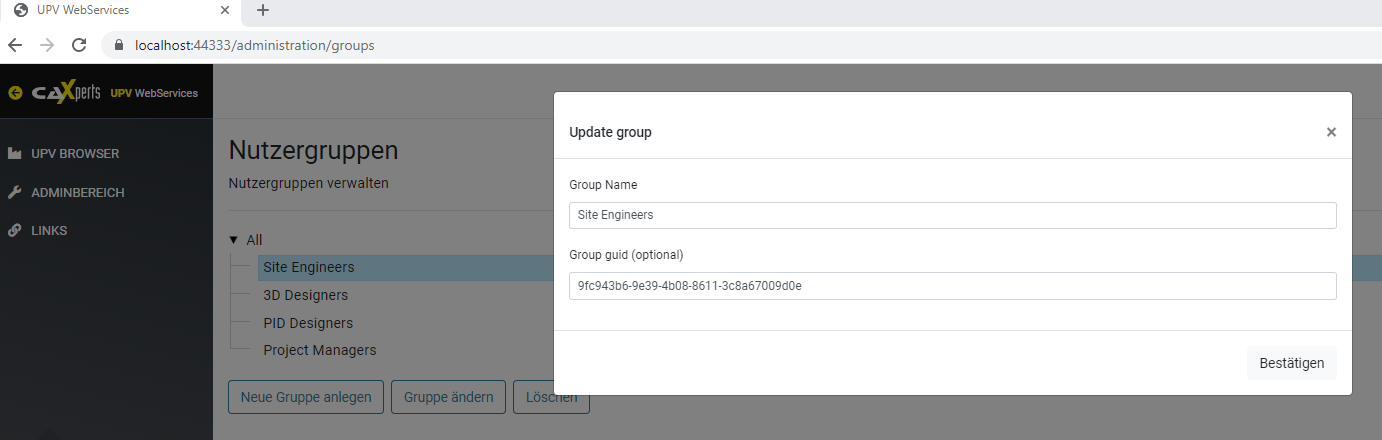
Create the groups to be synchronized in UPV WebServices portal at
../administration/groups Assign the Group
guid found in the Azure Portal to the new group. The group
connection is established using the guid value.
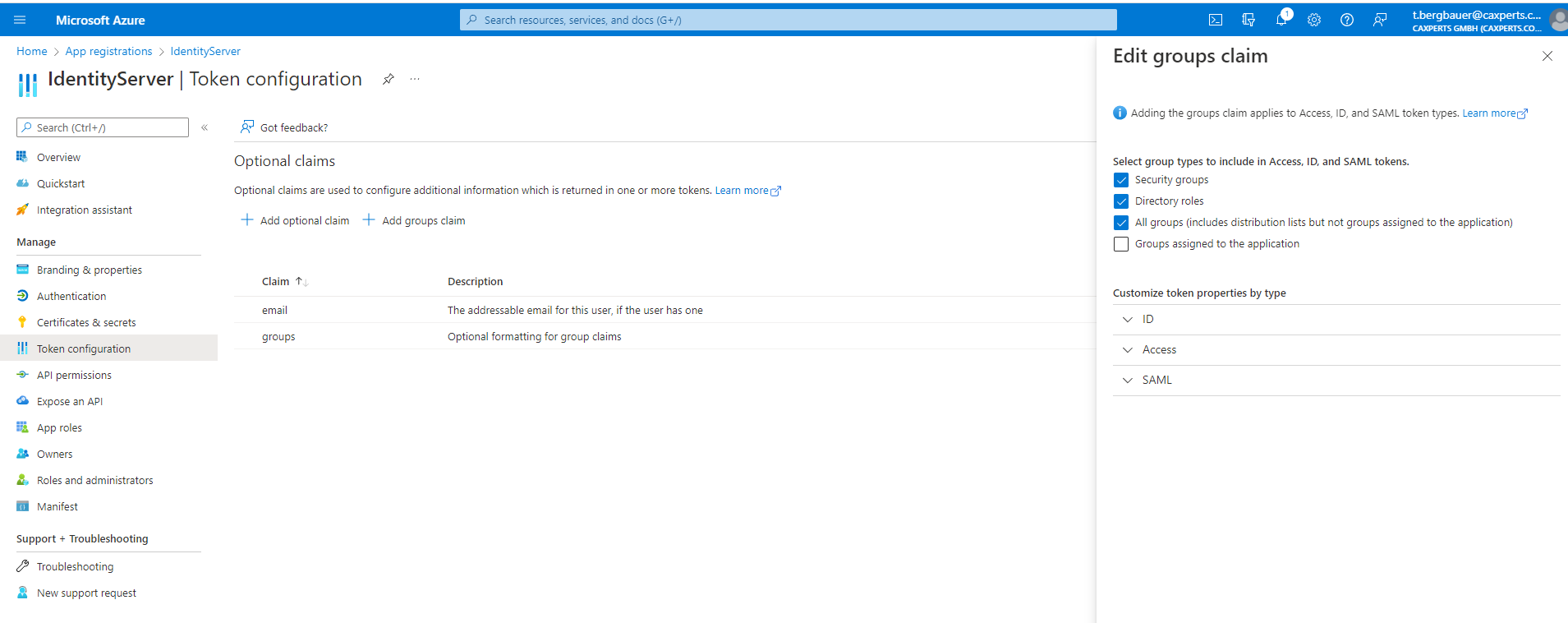
Allow requesting the group claim in the azure portal:
On the Token Configuration page
- add an additional groups claim
In the Keycloak Identity provider settings add a new entry at Mappers. This will transmit the information of the groups claim to the users attribute field. The UWS expects the attribute to be set as User attribute name with value groups. If your Identity providers group claim name differs from this convention, you can define the necessary Claim name in this mapper. Please note the Claim is case-sensitive.
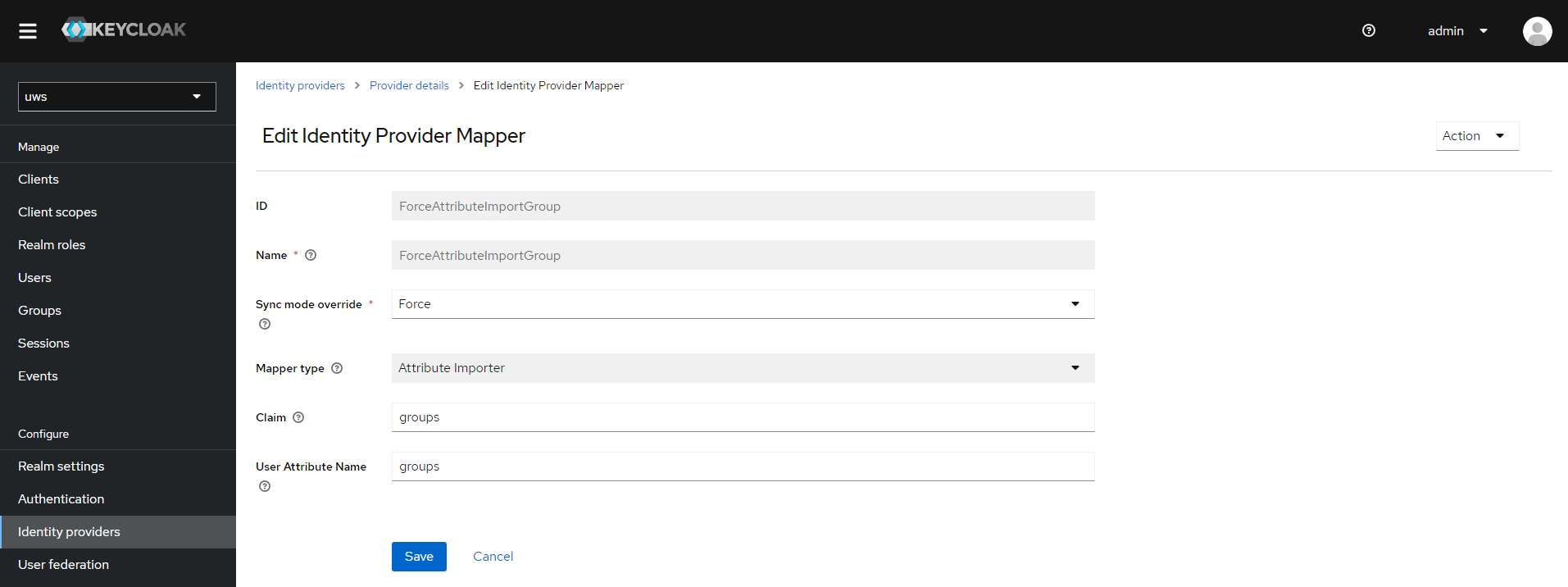
Sync mode: Defines when the mapper is executed
Options:
- Force: Updates on every login (recommended)
- Import: Updates only when the user is initially created in Keycloak
Import roles
You can use a new Mappers entry for this as well.
This is done using the Claim to Role mapper.
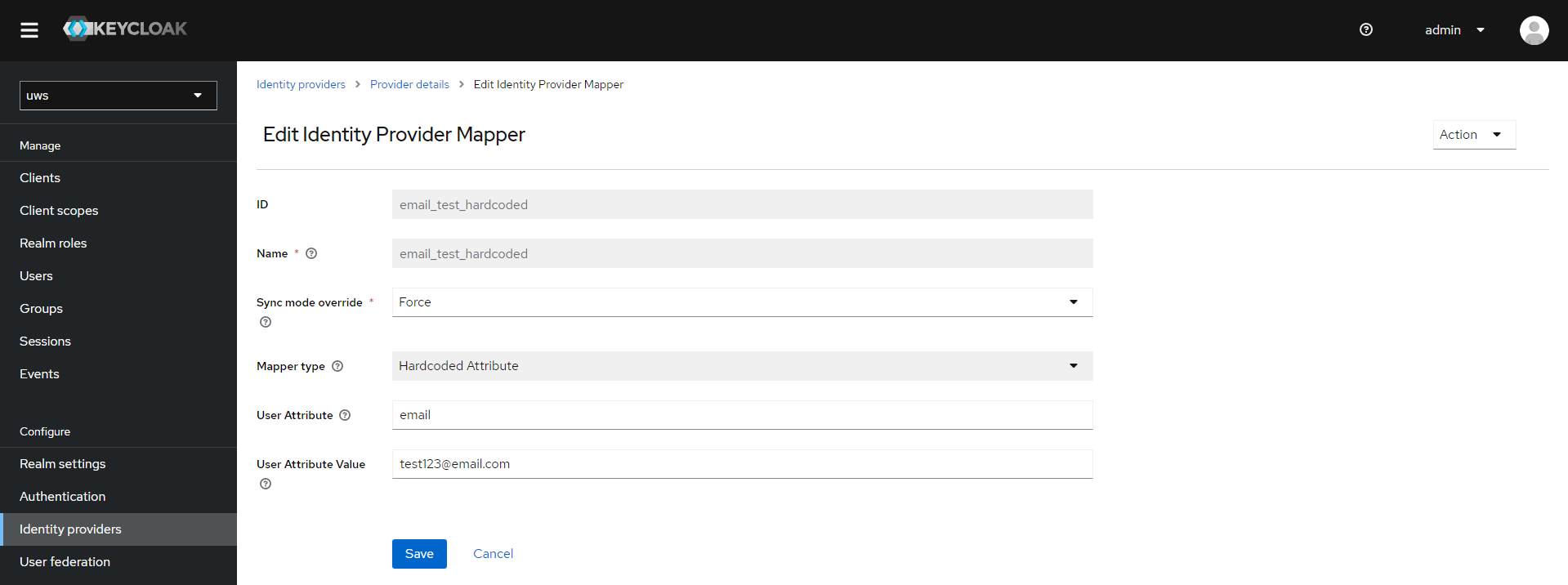
Metadata customization
You can use a new Mappers entry for this as well.
This is done by providing the desired User attributes. Relevant predefined mappers for this use case would be Attribute Importer and Hardcoded Attribute. So f.e. when providing a user attribute named email, this will correspond to the users email entry.
Keycloak claims:
- username
- firstName
- lastName
- emailVerified (seems not to work at the moment)
Troubleshooting
You can use following keycloak start command to enable logging of user claims on login:
kc.bat start --log-level="INFO,org.keycloak.social.user_profile_dump:debug"